Aug 20, 2024
Decentralized Identity and Consent: The Key to User Privacy and Compliance

Privacy awareness is on the rise, driving the demand for effective privacy solutions.
AesirX Shield of Privacy meets this need by integrating decentralized identity with user consent.
This approach gives individuals greater control over their data while aiding organizations in achieving compliance with regulations like GDPR [1] and the ePrivacy Directive [2].
This article explores how the combination of decentralized identity and consent creates a secure and transparent environment that prioritizes user privacy.

What Is Decentralized Identity?
Decentralized identity is a digital identity system that gives individuals control over their personal information.
Unlike traditional identity systems, which rely on centralized authorities to manage and verify identities, decentralized identity allows users to store and manage their credentials securely on their devices.
This means that individuals can share only the necessary information with organizations, reducing the risk of data breaches and enhancing privacy.
Here’s How Decentralized Identity Works:
- Blockchain Foundation: Decentralized identity uses blockchain technology to securely store personal information. This ensures the data is tamper-evident and reliable. For example, Alice’s personal details are stored on a blockchain. When she needs to verify her identity for an online service, the service checks the blockchain to confirm her information without seeing the actual data. This process ensures Alice’s information is secure and trustworthy.
- Self-Sovereign Identity (SSI): SSI ensures that individuals own and control their credentials without needing external validation. It promotes digital autonomy, allowing users to manage their identities as they see fit. For example, John has an SSI. When he wants to access a new website, he uses his own credentials stored on his device to verify his identity, without needing to involve a third party like a government or company. This way, John manages his identity on his own terms.
AesirX Shield of Privacy's Decentralized Identity
AesirX Shield of Privacy utilizes Concordium blockchain ID and Zero-Knowledge Proof (ZKP) technology to enhance user privacy and security.
This combination allows individuals to verify their identity without revealing unnecessary personal information, further enabling users to control their data while ensuring compliance with privacy regulations.
By utilizing these advanced technologies, AesirX creates a more secure and trustworthy environment for managing digital identities.
AesirX Shield of Privacy's Decentralized Identity
Advantages of Decentralized Identity for User Consent
Decentralized identity enhances consent frameworks by changing how personal information is managed and shared. Here are the key advantages:
- User Consent: Entities must seek explicit consent from users before accessing personal details, as required by laws like GDPR. Decentralized identity facilitates this process, allowing users to control who accesses their data.
- Security: Digital identities are difficult to forge or hack, significantly reducing the risk of impersonation and enhancing personal data security.
- Privacy Control: Users maintain control over when and how their identities are used, reviewing requests and disclosing only necessary information to protect their privacy.
- Transparency: Decentralized identity keeps a detailed log of when and where digital identities are used. This transparency fosters trust between users and the entities accessing their information.
Advantages of decentralized identity and consent for user control
Key Features of AesirX Shield of Privacy’s Decentralized Identity and Consent
- Granular Consent: AesirX Shield of Privacy enables users to specify which attributes to share with different entities, eliminating blanket permissions and ensuring only relevant data is disclosed.
- Immutable Audit Trail: Every consent decision is recorded on the Concordium blockchain, providing a clear and verifiable history of consent activities.
- Revocation Control: Users can revoke consent instantly if preferences change, ensuring that their choices are respected at all times.
User Consent in AesirX’s Decentralized Identity Framework
AesirX provides a comprehensive consent model for website visitors, offering three straightforward options:
- Users can choose to reject data collection entirely,
- Explicitly consent to tracking,
- Or opt for the decentralized consent option, which gives them greater control over their personal data while allowing them to earn rewards from Share2Earn, Contribute2Earn and Affiliate2Earn.
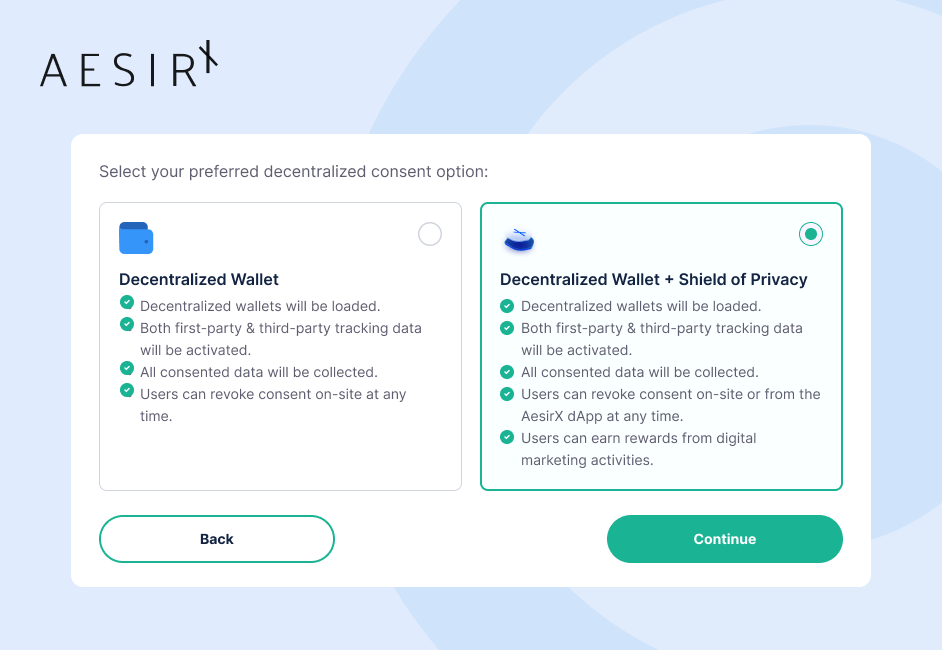
The decentralized consent option seamlessly integrates decentralized identity with consent management and operates through two methods:
- Decentralized wallet: Allows users to manage their consent directly.
- Decentralized wallet + Shield of Privacy: Adds an extra layer of protection by pseudonymizing user identities.
AesirX’s decentralized identity and consent framework includes several key components. First, the Shield of Privacy pseudonymization layer masks user data, ensuring that identities remain protected during interactions with websites. Additionally, the Shield of Privacy (SoP) ID is securely linked to the domain name, facilitating secure consent registration and establishing a legal audit trail.
How it Works
Step 1: When visiting a website, users receive a clear request to sign a consent form.
Step 2: Upon signing, their consent is securely recorded on the blockchain.
Step 3: Users can review and change their consent preferences anytime using the AesirX decentralized application (dApp).
AesirX Shield of Privacy’s Decentralized Identity and Consent
Step-by-Step Guide to Implementing User Consent in Decentralized Identity for Your Website
Implementing consent in a decentralized identity framework involves integrating AesirX's first-party analytics and the Shield of Privacy. Follow these steps:
1. Sign Up and Obtain an AesirX Analytics License
- Visit the AesirX Sign-Up Page to create an account.
- Complete the registration process by filling in the required information and selecting First-Party Analytics.
- After confirming your registration, receive your license ID via email. This ID is necessary for configuring AesirX Analytics.
2. Integrate AesirX Analytics
- Custom Development: Follow AesirX instructions to embed the analytics code directly into your website's HTML.
- WordPress or Other CMS: Download and install the AesirX Analytics plugin/module from GitHub. Activate the plugin and configure the settings for server setup, consent options, and data collection preferences.
For detailed instructions, refer to our implementation guides and support resources.
3. Configure Consent Management
- Customize the consent banners within the AesirX dashboard.
- Choose from two consent mode templates that align with your policies and brand.
- Or, adjust the consent mode templates during the analytics consent setup. See the detailed instructions.
Enhancing User Consent with AesirX’s Decentralized Identity Solutions
To implement consent management on your website, follow the simple steps outlined in this guide. By integrating AesirX's first-party analytics and the Shield of Privacy, you can create a safe and transparent environment that prioritizes user privacy.
Ready to get started? Sign up for AesirX today and give your users the privacy and control they deserve.
Sources: